Threats to Cloud Security. Cloud computing is on the rise and becoming popular in the public and business enterprises sector. Many CSPs (Cloud Service Providers) like, Microsoft Azure, AWS (Amazon Web Service), and GCP (Google Cloud Platform) are offering their clients and users the opportunity to migrate the operations to the cloud by subscribing services () that fits their operation needs. There are many activities involved with migrating to the cloud that are important for the public and business enterprises to understand before making such leap (migrate). Speaking of migrating, the term security is one of the most critical aspects that concerns cybersecurity team members, and all proper measures must be taken seriously. The uprising of cyber threats to cloud computing increases by the day just as cloud computing becomes more and more popular. The following are lists of threats to cloud security: 1. Data Breach - regardless o...
Posts
Showing posts from October, 2023
- Get link
- X
- Other Apps
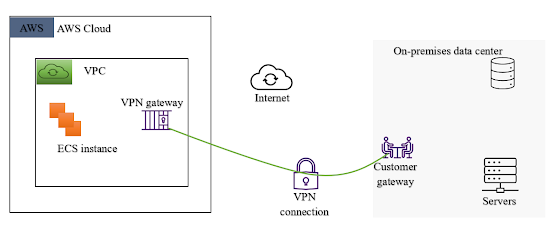
Hybrid Cloud and Multi-Cloud Networking Objectives: Hybrid Cloud and Multi-Cloud Networking, The Different Between Virtual Private Network and Direct Connect. 1. Hybrid Cloud and Multi-Cloud Networking The purpose for this blog article is to discuss some helpful tips regarding hybrid cloud and multi-cloud networking, and the differences between VPN (Virtual Private Network) and Direct Connect – the important role both methods play in connecting network. A hybrid cloud is a network infrastructure that exists in two different places – on-prem and in the cloud. Like hybrid clouds is multi-cloud which is a network infrastructure that’s dedicated to two or many different platforms like, AWS (Amazon Web Service), GCP (Google Cloud Platform), or Microsoft Azure and Salesforce. With all these different platforms, one could wonder about the notable complexity in making these different network services and tools to communicate to and assist each other. The...
- Get link
- X
- Other Apps
Week 6: Cybersecurity Threat This week’s blog discussion focuses on a broad variety of new cybersecurity threats that do exist. We live in an age where cybersecurity threats are becoming increasingly imperative – this doesn’t mean that cybersecurity threats of the past weren’t as imperative as cybersecurity threats of today. The difference is that cybersecurity threats in this current stage are far more sophisticated than in the past due to the innovation evolution of technology. As cybersecurity teams tighten their defenses lines with the state-of-the art technology to prevent and mitigate security threats (penetration) from cyber criminals, in return, cyber criminals are researching sophisticated methods that can penetrate those lines of security defenses. The following are lists of some new cybersecurity threat courtesy of trellix.com: 1. Cyberespionage Events Targeting Southeast Asian Government Linked To Statel...
- Get link
- X
- Other Apps
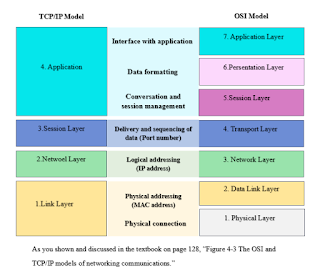
Week Five: Cloud Networking This week objectives covered an array of topics like, Networking Concepts in the Cloud, which is in conjunction to, Networking Concepts, From OSI Model to Cloud Stack, and Software-Defined Networking in the Cloud to IP Address Space, also in conjunction also to IP Addressing, Subnetting, Cloud Network Interfaces, and many more. Let’s dive into discussing some little but important aspects and details that are associated with some of the topics listed above. You can always pursuit other articles throughout the Internet to be better orientated for your preferences. Networking Concepts in the Cloud 1. The OSI Model to Cloud Stock: The OSI (Open System Interconnection) Model and the TCP/IP (Transmission Control Protocol/Internet Protocol) Model have some similar features and operations, just like every other technology we utilized. The TCP/IP and the OSI models work hands-in-hand to allow the flo...