Week 10 Blog: Cloud Storage Regardless of whether we are working in the cloud or on-prem, managing enterprise-scale network, working on a research document on our home computer, we are in the loop of creating, saving, and accessing data. Data is anything created and saved on a storage device through electronic device (computer). You may ask yourself why IT exists? The simple will be, IT exists to solve problems, and to manage data. Companies that invest well in their IT infrastructure outweigh those in their respective industries that don’t. Nearly every business decision hinges on the quality of data made available to decision makers (West, 2023, p. 303). That said, File, Block, and Object storage play important roles in the data storage process. Each storage contributes and is efficient in their respective environments if utilized accordingly. Fully acknowledging the critical role that data plays in business clearly state the need for implementing effective data s...
Posts
- Get link
- X
- Other Apps
Week 9 Blog: Single-Sign-on Authentications I have the opportunity of learning about a new authentication method for the very first time, so, I have decided to use this blog post to discuss as much as possible to explain some details about the authentication method. The authentication method in which I am speaking of is none other than Single Sign-On authentication. First, before going any further, “authentication is a process usually managed by a server that proves the identity of a client (which could be a user, service, or application) and determines whether that client is allowed to access a secured system.” To validate the very identity of any client, there must be some kind of “directory service” implemented in place to manage all the database account information associated with the client “usernames, passwords, and other authentication credentials.” Authentication In addition to speaking about authentication, there must be an effective password policy implem...
- Get link
- X
- Other Apps
Threats to Cloud Security. Cloud computing is on the rise and becoming popular in the public and business enterprises sector. Many CSPs (Cloud Service Providers) like, Microsoft Azure, AWS (Amazon Web Service), and GCP (Google Cloud Platform) are offering their clients and users the opportunity to migrate the operations to the cloud by subscribing services () that fits their operation needs. There are many activities involved with migrating to the cloud that are important for the public and business enterprises to understand before making such leap (migrate). Speaking of migrating, the term security is one of the most critical aspects that concerns cybersecurity team members, and all proper measures must be taken seriously. The uprising of cyber threats to cloud computing increases by the day just as cloud computing becomes more and more popular. The following are lists of threats to cloud security: 1. Data Breach - regardless o...
- Get link
- X
- Other Apps
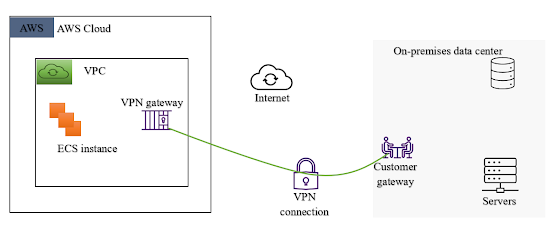
Hybrid Cloud and Multi-Cloud Networking Objectives: Hybrid Cloud and Multi-Cloud Networking, The Different Between Virtual Private Network and Direct Connect. 1. Hybrid Cloud and Multi-Cloud Networking The purpose for this blog article is to discuss some helpful tips regarding hybrid cloud and multi-cloud networking, and the differences between VPN (Virtual Private Network) and Direct Connect – the important role both methods play in connecting network. A hybrid cloud is a network infrastructure that exists in two different places – on-prem and in the cloud. Like hybrid clouds is multi-cloud which is a network infrastructure that’s dedicated to two or many different platforms like, AWS (Amazon Web Service), GCP (Google Cloud Platform), or Microsoft Azure and Salesforce. With all these different platforms, one could wonder about the notable complexity in making these different network services and tools to communicate to and assist each other. The...
- Get link
- X
- Other Apps
Week 6: Cybersecurity Threat This week’s blog discussion focuses on a broad variety of new cybersecurity threats that do exist. We live in an age where cybersecurity threats are becoming increasingly imperative – this doesn’t mean that cybersecurity threats of the past weren’t as imperative as cybersecurity threats of today. The difference is that cybersecurity threats in this current stage are far more sophisticated than in the past due to the innovation evolution of technology. As cybersecurity teams tighten their defenses lines with the state-of-the art technology to prevent and mitigate security threats (penetration) from cyber criminals, in return, cyber criminals are researching sophisticated methods that can penetrate those lines of security defenses. The following are lists of some new cybersecurity threat courtesy of trellix.com: 1. Cyberespionage Events Targeting Southeast Asian Government Linked To Statel...
- Get link
- X
- Other Apps
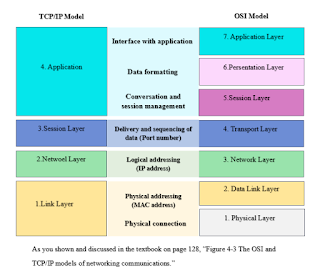
Week Five: Cloud Networking This week objectives covered an array of topics like, Networking Concepts in the Cloud, which is in conjunction to, Networking Concepts, From OSI Model to Cloud Stack, and Software-Defined Networking in the Cloud to IP Address Space, also in conjunction also to IP Addressing, Subnetting, Cloud Network Interfaces, and many more. Let’s dive into discussing some little but important aspects and details that are associated with some of the topics listed above. You can always pursuit other articles throughout the Internet to be better orientated for your preferences. Networking Concepts in the Cloud 1. The OSI Model to Cloud Stock: The OSI (Open System Interconnection) Model and the TCP/IP (Transmission Control Protocol/Internet Protocol) Model have some similar features and operations, just like every other technology we utilized. The TCP/IP and the OSI models work hands-in-hand to allow the flo...
- Get link
- X
- Other Apps
Migration to the Cloud - Part 2 In Part One of Migrating to the Cloud was about Migration Planning where I discussed some various aspects regard: Cloud Migration Phases, Transition Assessment, Migration Plan, Migration Strategies, and Timing. There are a variety of activities (Migration Planning, Migration Execution, Deployment Testing and Validation, Cloud Agility, Planning for Program, etc.) that are involved with cloud migration, and it is imperative that most, if not all these activities must be carefully considered to successfully migrate to the cloud. That said, this Part Two blog is about Cloud Agility, where I am going to focus my attentions on the three following aspects: Development and Testing, and Cloud Agility. Deployment Testing and Validation: 1. Testing Types – executing a test before the launch of any project is a must. Many of us have carry-out some forms of testing in our lifetime whether it be before during the ...